Ad fraud detection companies closely collaborate with ad tech businesses and this trend is not new. Investing their money in ad campaigns, advertisers and media buyers hope that they will receive only human traffic without any injections of bot traffic.
Theoretically, the advertising should be shown only to the target users. In reality, everything is slightly different and some of the impressions that advertisers track in their marketing analytics systems can be generated by bots or malicious programs. Mobile ad fraud and regular ad fraud can bring a lot of problems for marketers.
This problem needs some real-time solutions. Ad fraud detection techniques and scanners are designed to fix this problem and prevent it from happening on both supply and demand sides.
Let’s explore the landscape of modern ad fraud prevention tools and understand how they work, how to integrate them, and what is the difference between post-bid and pre-bid scanning.
Ad fraud detection techniques vs. 7 types of digital ad fraud
To start off with, desktop and mobile ad fraud techniques can also be different, but the main idea behind them is to generate fake clicks, impressions, or any sort of conversion.
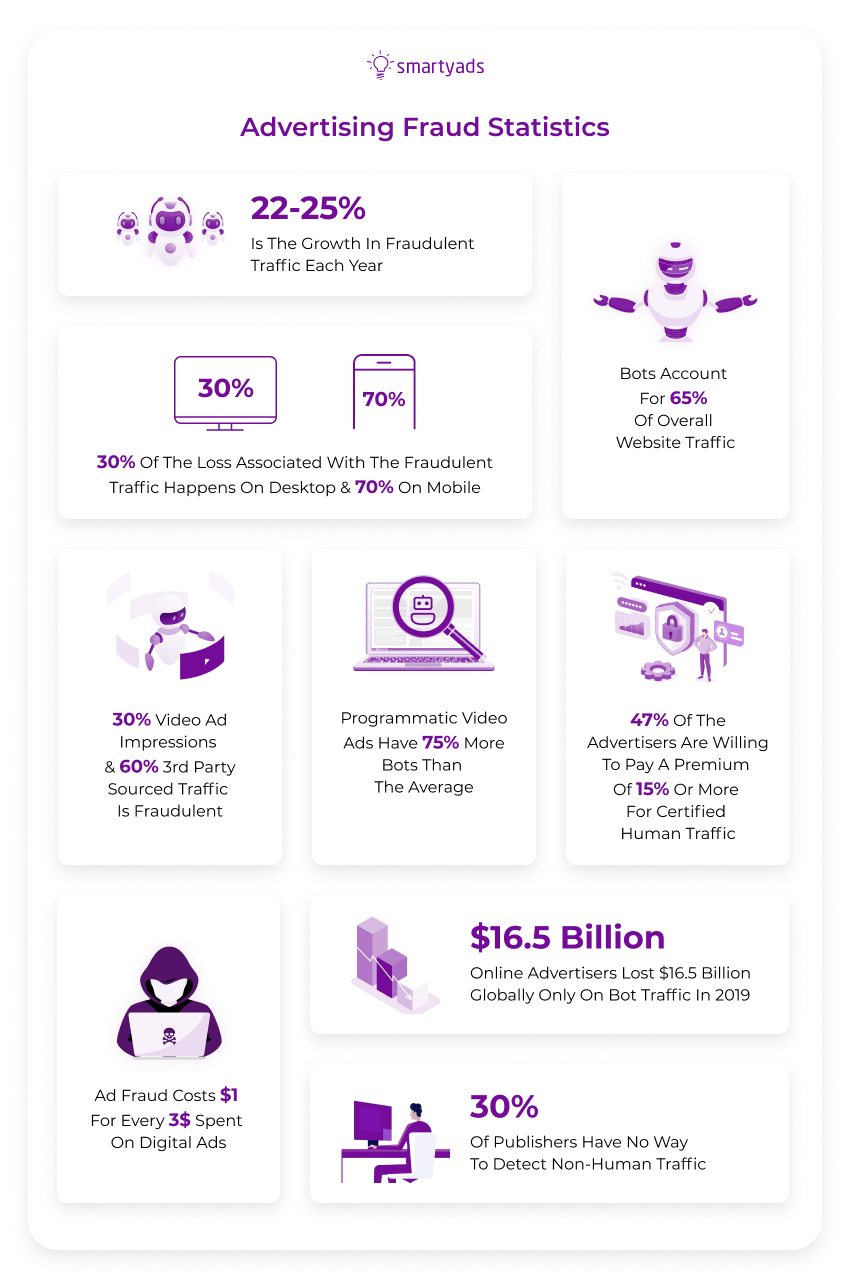
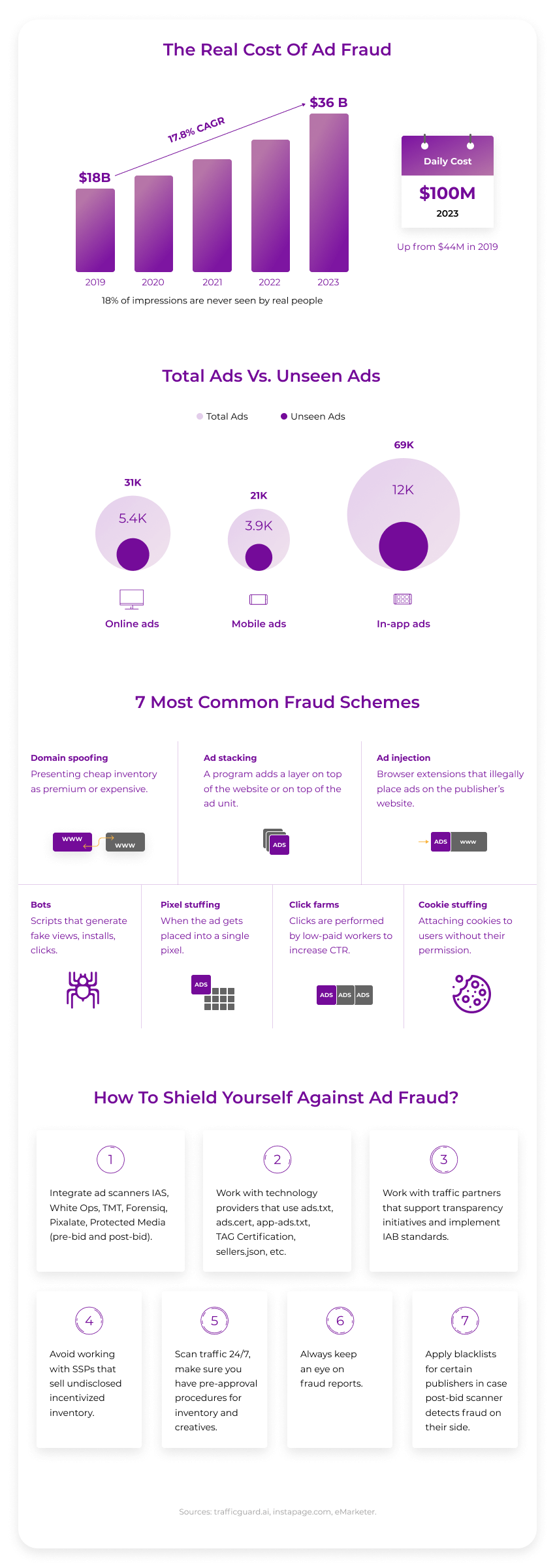
According to a study by Future Digital Advertising: Artificial Intelligence & Advertising Fraud 2019−2023, in four years without fraud protection tools, the daily cost of ad fraud will equal $100 million daily. For comparison, last year it accounted only for $44 million.
So, how do fraudsters benefit from ad fraud?
Some SSPs aggregate traffic from individual publishers and ad networks to maximize web traffic volumes. In such circumstances, it gets hard to keep an eye on all web traffic partners, let alone individual publishers each of which gets payment per action performed on their business site.
There’s always a chance that some players will try to overcome rules by resorting to the following types of digital ad fraud:
- Domain spoofing — the URL of the site where the ad is served gets misplaced. The ad server receives false positives about where the ad runs. Indeed, the impression takes place at cheaper inventory;
- Bots — the most common type that uses Internet scripts to generate all kinds of bot traffic click fraud, fake video views, and impressions;
- Pixel stuffing — when the ad gets placed into a single pixel;
- Ad stacking — a program uses a multi-layered approach and adds a layer on top of the website or on top of the ad unit;
- Click farms (device farms) — fake clicks are performed by low-paid workers to increase CTR;
- Ad injection — browser extensions that illegally place ads on the publisher’s website;
- Cookie stuffing — common in affiliate marketing; when cookies are filled with wrong data about users.
In order to get rid of all these malicious schemes, ad fraud prevention companies develop ad fraud detection techniques and scanners that now can be integrated into any kind of ad platform.
Mobile ad fraud
Fraud in mobile digital marketing is a frequent phenomenon and to protect mobile advertising campaigns, it's important to know how fraudsters work.
Common mobile ad fraud schemes
- Ads pseudo-attribution. In this scheme, bad guys — the owners of the resource — place several ads on top of one another. The visitor on the site sees only the top ad. If vendors pay per impression, the attackers will be rewarded for showing all the ads.
- Clickfraud. The main purpose of click fraud is to imitate the actions of real users in order to trick marketing analytics tools into believing that fraudulent clicks and fraudulent traffic are real. Can be performed with device farms (it uses many real devices to create non-human traffic).
- Click injection. It is one type of mobile ad fraud where malware is embedded on the device to track apps downloaded to it. Once the installation is complete, the malware manages to click it before the user launches it himself.
- Click-bombing (spamming). Using this scheme, the scammers bombard the app with clicks in order to capture attribution, i.e. they click (launch) it before the users do it themselves. Each click is assigned with a unique identifier that corresponds to the device ID of the real user who downloaded the advertised app.
- Device ID reset. This scheme involves a cycle of endless app installs and resetting the device ID on which it is downloaded. For the advertiser, this would mean that its product was downloaded each time by unique organic users.
- How it works: the scammer clicks on the ad, downloads the advertised app, installs it, performs some more actions in it, and then resets the device ID to do the same thing again. And they do this many times.
- App ID spoofing. Fraudsters use this cheating scheme like this: they run an ad in the fraudulent app, but the advertiser thinks it's showing in another app that was claimed when it was placed. Attackers simply change the parameters and provide fake or stolen identifiers.
- SDK spoofing. It is a mobile fraud scheme that involves bots and malware. An app embedded in another — the real one — will generate clicks and play other actions in it and sends it to the MMP (mobile measurement partner). This malicious scheme is very difficult to detect. Any application that uses the SDK is vulnerable to SDK spoofing.
- VPN as a fraudulent tool. For every five clicks on an ad, there is one performed using a VPN. This technology enables scammers to hide their location and display virtual unique IP addresses each time a new connection is made. This is how they bypass systems for blocking automated ad-skimming.
Ad fraud prevention. How the online advertising industry fights back
According to ANA (Association of National Advertisers), the estimated global economic damage from fraud in 2019 reached $5.8 billion.
In this case, the authors of the study recorded a downward trend for the first time and stated that the fight against fraudulent schemes is yielding results. In two years, the share of fake display ad impressions has decreased from 9% to 8%, and in video ads from 22% to 14%.
It happened after the broad introduction of ad fraud detection technology like Forensiq, Pixalate, TMT, IAS, and so on. DSPs and SSPs learned how to filter out suspicious or invalid traffic before the bid even takes place.
Thus, now clients can trust their programmatic budgets to platforms with early fraud detection systems that were developed only a few years ago. Additionally, in order to keep away from ad fraud, cybersecurity professionals also recommend adhering to the following practices:
- Work with technology providers that use ads.txt, ads.cert, app-ads.txt, TAG Certification, sellers.json, and other traffic and seller verification standards (SmartyAds has them in place);
- Work with SSPs that are ready to support transparency initiatives and implement IAB standards for their publishers;
- Avoid working with SSPs that sell undisclosed incentivized inventory;
- Scan the traffic for non-human traffic in your system with scanners that work 24/7, use DoubleClick bid manager;
- Make sure you have pre-approval procedures for inventory and creatives;
- Always keep an eye on fraud reports; generate them every week or every day to stay sure that traffic in your marketplace is 100% valid;
- Apply blacklists for certain publishers in case the post-bid scanner detects fraud on their side.
Features and characteristics of the modern ad fraud detection tool
A good ad fraud detection tool can significantly reduce ad fraud by automatically banning suspicious impressions and bots at the stage of bidding or prior. Such fraud prevention tools can be installed on both supply and demand sides to achieve a synergy of action.
Pre-bid scanners
It identifies fraud before the ad is served at the stage of request. Such scanning tools monitor and sort out requests before bidding, that’s why their cost can be slightly higher. However, scanners filter out invalid traffic before it is counted as an impression which makes such ad fraud detection tools the most reliable.
The post-bid scanners
It gives advertisers, agencies, and marketers an opportunity to investigate where a fraud source is at the stage of response. The tracking tags contained in creatives make it easy to understand which domains or creatives are fraudulent or compromise brand safety.
Such scanners work in real-time and detect pre-bid or post-bid suspicious activities, some tools can do both. However, this logic of fraudulent activity detection is intrinsic only to a certain type of scanners. Indeed, online ad fraud prevention techniques are highly diversified.
Ad fraud detection companies: types and principles of work
Ad fraud detection companies create ad fraud detection software or utilities, non-stop scanners, and whole software platforms to protect the advertising ecosystem from scammers. Let’s review the most popular of them.
Pixalate and Protected Media scanners
Pixalate uses big data analysis, created by data scientists, to identify characteristic signs of online advertising fraud. Thanks to machine learning technologies, the scanner interprets the new fraudulent methods and defines particularly sophisticated schemes applying the scanning techniques we discussed above. Their technologies work across display, in-app, video, and OTT/CTV environments.
Pixalate is a supply scanner, supported by SmartyAds Solutions, and uses img pixels and all types of macroses for traffic scanning (which platform owners can select for themselves).
Scanner from Protected Media is also based on smart artificial intelligence and machine learning technologies for fraud detection scanning. It prevents fraud from happening before the impression takes place and post-bid gives insights into specific ad fraud sources. The scanner works for Connected TV, Display, and Video advertising.
Protected Media is a supply scanner but on SmartyAds Solutions it enables platform owners to scan traffic on SSP endpoints before DSPs reach it. You can easily prevent bad traffic with a scanner and monitor it with post-bid functionality.
Since we have an active partnership with Protected Media in place, you don’t have to negotiate integration with this ad fraud detection provider directly. Just make a request and in 7 days you will be able to turn pre and post-bid scanners in your system using SmartyAds credentials.
Forensiq scanner
The Forensiq scanner is designed to mitigate affiliate fraud, traffic fraud, and abnormalities. It assesses every impression according to the proprietary fraud score metric and evaluates the potential viewability and brand safety score of the traffic source.
The solution provides a full-funnel invalid traffic detection (SIVT & GIVT accredited) across various traffic channels and effectively protects inventory from bad actors.
SmartyAds has recently partnered with Forensiq which means that the scanner is now available for your SmartyAds Solutions. You can turn it on in the dashboard, configure it in accordance with your needs, and generate regular reports to see how it deals with your traffic threats.
TMT Scanner
TMT scanner is a solution that focuses on ad fraud prevention on the demand and supply side. It offers fraud prevention, media filters for integration, malware attack data, creative and website quality assurance, customers hack prevention, and digital insights on fraud occurrence. TMT closely collaborates with IAB and the world’s largest media owners.
TMT scanner can also function in your SmartyAds Solutions but in order to turn it on for your system, you need to negotiate prior to installation. After this, you will be able to turn it on and set up the daily limits of scans (see the screen above).
IAS Integral Ad Science
The IAS scanners (stand for Integral Ad Science) are also featured among the best ad fraud detection companies for advertisers and publishers alike.
This company provides ad fraud solutions that are accredited by MRC for SIVT (Sophisticated Invalid Traffic) detection. IAS allows the delivery of verified inventory. The three stages of traffic verification they use are ad networks scanning, behavioral patterns detection on real devices, and malware check that will work across all traffic channels.
White Ops
White Ops is a cybersecurity company; their solutions protect publishers and advertisers from the majority of threats associated with ad fraud. White Ops is one of the largest fraud detection companies that’s been in charge of protecting traffic of Oath and Adobe and other big ad tech industry players since 2012.
White Ops solutions are MRC accredited and can be used by advertisers and publishers who want to eliminate invalid inventory across environments (desktop and mobile) and verticals (especially in travel, retail and financial ones).
Making sure your SmartyAds Solutions is brand-safe and secure
We want to remind our clients that we collaborate with the world’s best ad fraud detection companies and regularly partner up with new ones to outsmart even the most sophisticated fraudulent schemes. We want to keep our publishers and advertisers as safe as possible.
Advanced cybersecurity scanners that we provide to you are focused on both ad fraud prevention and detection. Moreover, we offer API key implementation so that you could integrate any scanner of your choice and keep your traffic safe and secure.
If you need an individual implementation of any scanner, please be sure to notify us about your needs.
The last word
Ad fraud detection tools will not cease to develop as long as advertising space is plagued with bot traffic, ad click fraud, and fake views. Taking the fact that programmatic actively expands to new environments, e.g OTT/CTV or audio, in the future, the variety of ad fraud schemes will only grow.
The sooner ad tech providers (and also publishers and advertisers) realize the real state of things, the better trading environment they will be able to create for their direct advertisers and publishers and the higher incomes of money they will be able to generate in the end.